
Cost of cybercrime has surged by 800% in the past decade
The state of cybercrime in the U.S.
Since 2011, the number of cybercrime complaints received by the FBI has more than doubled, a recent survey found that more than four in 10 Americans had been the victim of cybercrime, and about half of all small businesses have experienced an attack or attempted attack in the past year.
Hacking, phishing, identity theft, tech support fraud — whatever form the attack takes, cybercrime is increasingly costly to American families and businesses. In 2020 alone, the total cost of cybercrime reported to the FBI topped $4 billion. And even the methods people often use to keep themselves safe, such as video cameras, are increasingly being targeted by cyber attackers.
Ensuring you’re able to keep your home or business secure from cybercrime means understanding what these incidents look like and how likely you are to be a target. Our analysis of federal cybercrime data found that:
- The total cost of cybercrime incidents reported to the FBI has gone up by nearly 800 percent since 2011.
- Incidents rose from a low of about 263,000 in 2013 to almost 800,000 in 2020, largely as a result of the pandemic.
- Phishing attacks are the most common method, while business email compromise is by far the costliest per incident.
Read on for our full analysis of 2020 internet crime data, as well as our tips for keeping your home or business secure.
Cybercrime by year (AKA the rise of phishing)
The number of cybercrime incidents reported to the FBI’s Internet Crime Complaint Center (IC3) has more than doubled over the past decade, and 2020 marked a nearly 70 percent increase in reports, likely related to the pandemic.
In addition to becoming more common, cybercrimes have become more costly, with total losses surging by 765 percent since 2011.
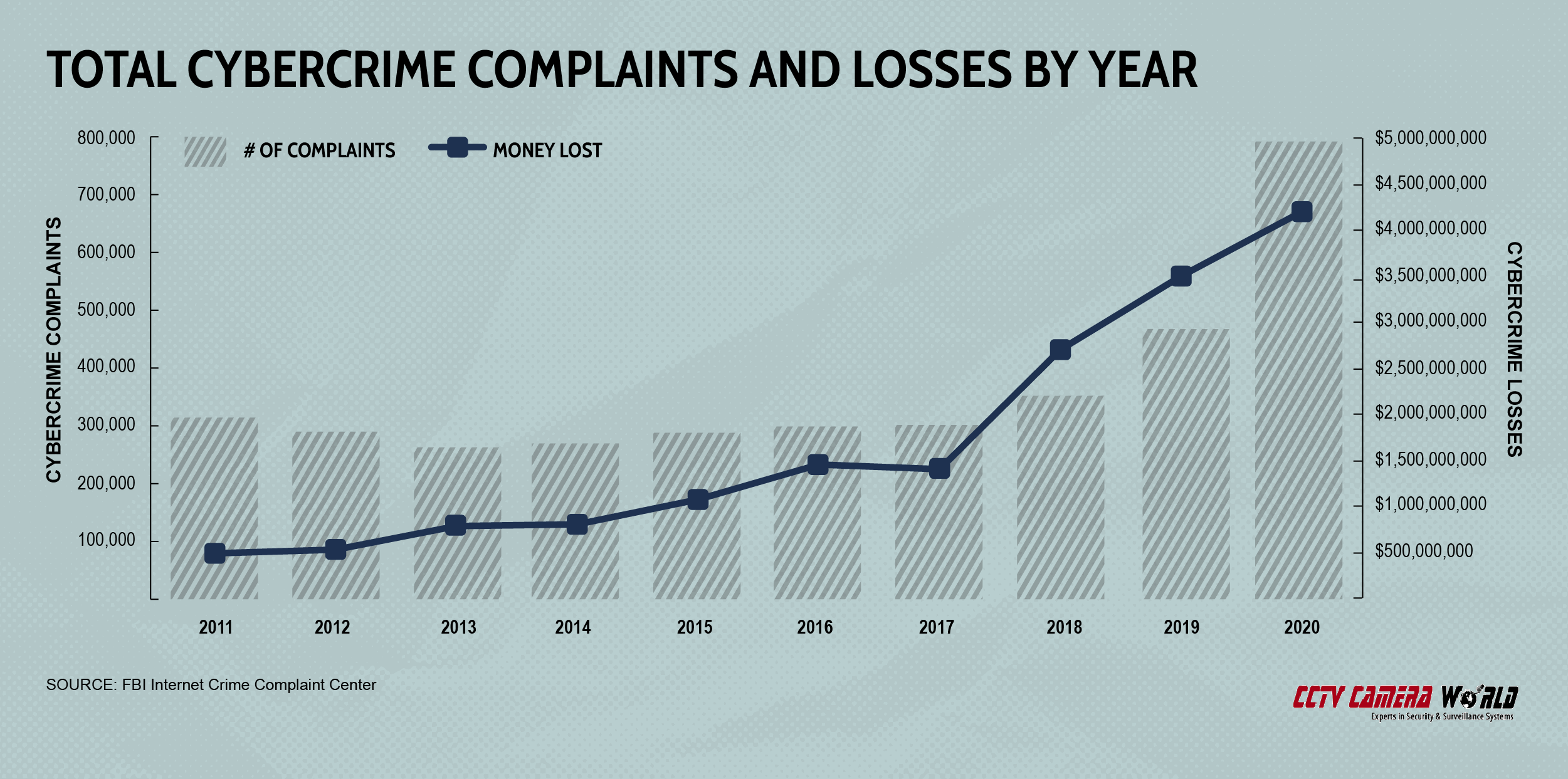
| Year | Complaints | Losses |
|---|---|---|
| 2011 | 314,246 | $485,300,000 |
| 2012 | 289,874 | $525,400,000 |
| 2013 | 262,813 | $781,800,000 |
| 2014 | 269,422 | $800,500,000 |
| 2015 | 288,012 | $1,070,700,000 |
| 2016 | 298,728 | $1,450,700,000 |
| 2017 | 301,580 | $1,400,000,000 |
| 2018 | 351,937 | $2,700,000,000 |
| 2019 | 467,361 | $3,500,000,000 |
| 2020 | 791,790 | $4,200,000,000 |
The shape of cybercrime has also changed as consumers and security providers have caught onto particular tactics, forcing criminals to change their methods.
In 2016, the most common type of cybercrime reported to the FBI was a non-payment or non-delivery crime, which are incidents in which goods or services are sent but payment is never made or vice versa (payments made but goods never provided). By 2020, non-payment/non-delivery crimes had fallen to a distant second thanks to the rise of phishing.
The FBI’s data classifies phishing alongside three related attack types — vishing, smishing and pharming. They’re grouped together because the basic premise is the same. An individual is contacted by what appears to be a legitimate company that requests login credentials or some other personal or financial information.
What distinguishes them is the contact method; phishing refers to email attacks, vishing and smishing refer to text message/mobile phone call attacks, and pharming refers to fraudulent website attacks. Over just the past half-decade, phishing and related attacks have climbed by more than 1,100 percent.
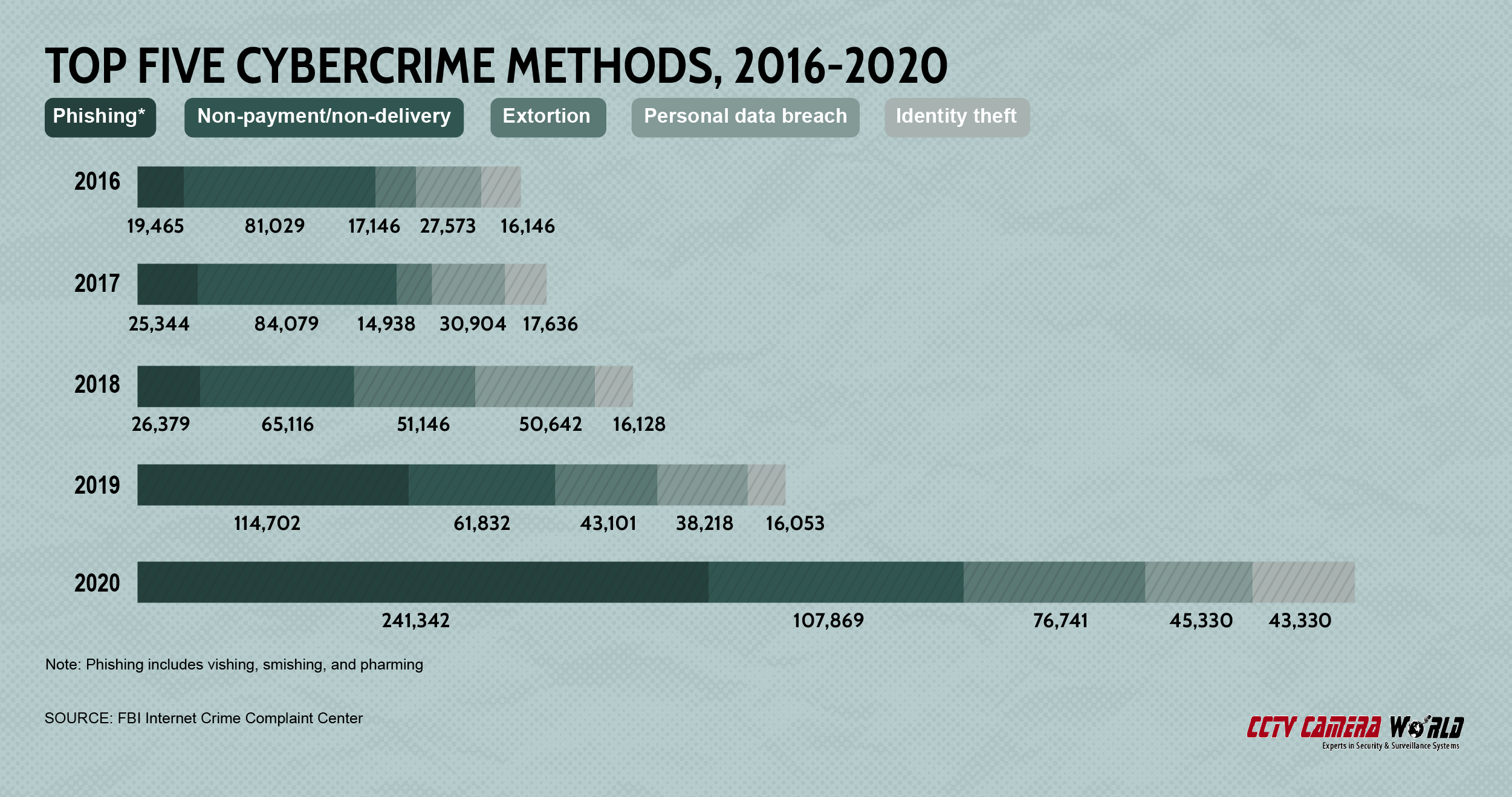
| Year | Phishing/vishing smishing/pharming |
Non-payment/ non-delivery |
Extortion | Personal data breach | Identity theft |
|---|---|---|---|---|---|
| 2016 | 19,465 | 81,029 | 17,146 | 27,573 | 16,787 |
| 2017 | 25,344 | 84,079 | 14,938 | 30,904 | 17,636 |
| 2018 | 26,379 | 65,116 | 51,146 | 50,642 | 16,128 |
| 2018 | 114,702 | 61,832 | 43,101 | 38,218 | 16,053 |
| 2020 | 241,342 | 107,869 | 76,741 | 45,330 | 43,330 |
According to FBI researchers, almost 30,000 of the complaints the agency received about cybercrime in 2020 were directly related to the COVID-19 pandemic, as fraudsters targeted federal and state funding, including stimulus payments and business loans.
One of the most common end results of business email attacks is deploying ransomware, which installs malware on a device when a file is opened or a link is clicked. The malware holds hostage the target’s data until the ransom is paid. If it’s not paid, the attacker may threaten to destroy the data or release it publicly. Though it’s a relatively new tool in their arsenal, fraudsters’ ransomware attacks are growing more sophisticated and targeted, and the results have been serious.
A ransomware attack in the spring of 2020 forced a shutdown of Colonial Pipeline, the largest gasoline pipeline in the U.S. Higher fuel prices, shortages, and gasoline hoarding all quickly spread to many parts of the country.
It’s also worth noting that all of the data we’re exploring in this story comes from incidents reported to the FBI’s cybercrime specialists. That doesn’t account for the unknown number of incidents that are never reported. As it is, the average ransomware attack costs almost $12,000 per incident, and the real number is almost certainly higher. The FBI has suggested that only 15 percent of all fraud victims report the incidents to law enforcement.
Global ransomware attacks are projected to cost about $20 billion this year alone and over the next decade, costs will surge to about $265 billion per year, as incidents become more common and many companies begin to consider ransomware a cost of doing business.
A closer look: Cybercrime losses
California, New York, and Texas, the three largest states by population, accounted for almost $1.4 billion cybercrime losses combined in 2020, with about $600 million in losses in California alone. But on a per-capita basis, the costliest state for cybercrime was North Dakota. There, the average cybercrime victim reported losses of nearly $34,000. No other state’s average cybercrime loss was even half as much. But even after balancing for population differences, California and New York are still in the top 10 and Texas ranks 11th.
The lowest loss amount was in Kentucky, where the average victim lost just under $1,200.
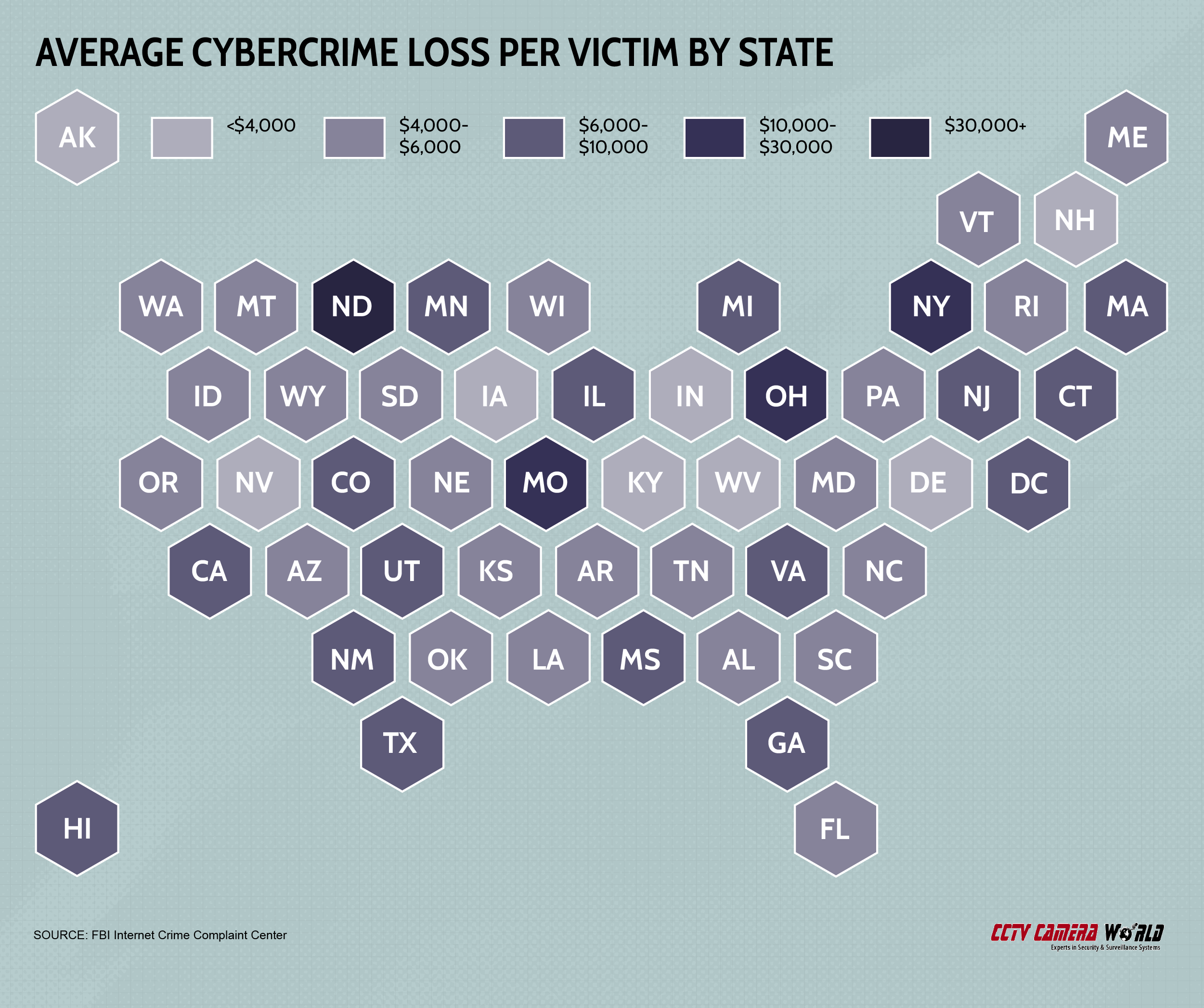
Average cybercrime loss per victim
| North Dakota | $33,954 |
| Missouri | $14,205 |
| Ohio | $12,680 |
| New York | $12,051 |
| Utah | $9,564 |
| California | $8,936 |
| District of Columbia | $8,885 |
| Minnesota | $8,521 |
| Massachusetts | $8,509 |
| Colorado | $8,167 |
| Texas | $8,115 |
| Illinois | $7,456 |
| Virginia | $7,383 |
| Georgia | $7,369 |
| Connecticut | $7,330 |
| Mississippi | $7,309 |
| New Mexico | $6,975 |
| Hawaii | $6,912 |
| Michigan | $6,709 |
| New Jersey | $6,658 |
| Pennsylvania | $5,822 |
| North Carolina | $5,679 |
| Oregon | $5,631 |
| Wyoming | $5,582 |
| Arizona | $5,545 |
| Kansas | $5,542 |
| Florida | $5,485 |
| Nebraska | $5,448 |
| Idaho | $5,283 |
| Louisiana | $5,263 |
| Washington | $5,109 |
| Vermont | $4,878 |
| Alabama | $4,747 |
| Tennessee | $4,713 |
| Rhode Island | $4,573 |
| Wisconsin | $4,343 |
| Oklahoma | $4,336 |
| South Carolina | $4,313 |
| Maine | $4,230 |
| Maryland | $4,220 |
| Montana | $4,153 |
| South Dakota | $4,129 |
| Arkansas | $4,100 |
| Alaska | $3,542 |
| Delaware | $2,909 |
| Nevada | $2,755 |
| Indiana | $2,751 |
| West Virginia | $2,536 |
| New Hampshire | $2,456 |
| Iowa | $2,284 |
| Kentucky | $1,848 |
Business email compromise (BEC), which can impact professionals’ business emails as well as their personal accounts in an attempt to conduct fraudulent wire transfer payments, is the costliest cybercrime type, though it was the eighth most common by overall numbers in 2020. Still, the average BEC attack cost almost $100,000. The second costliest type, corporate data breach, also affects businesses.
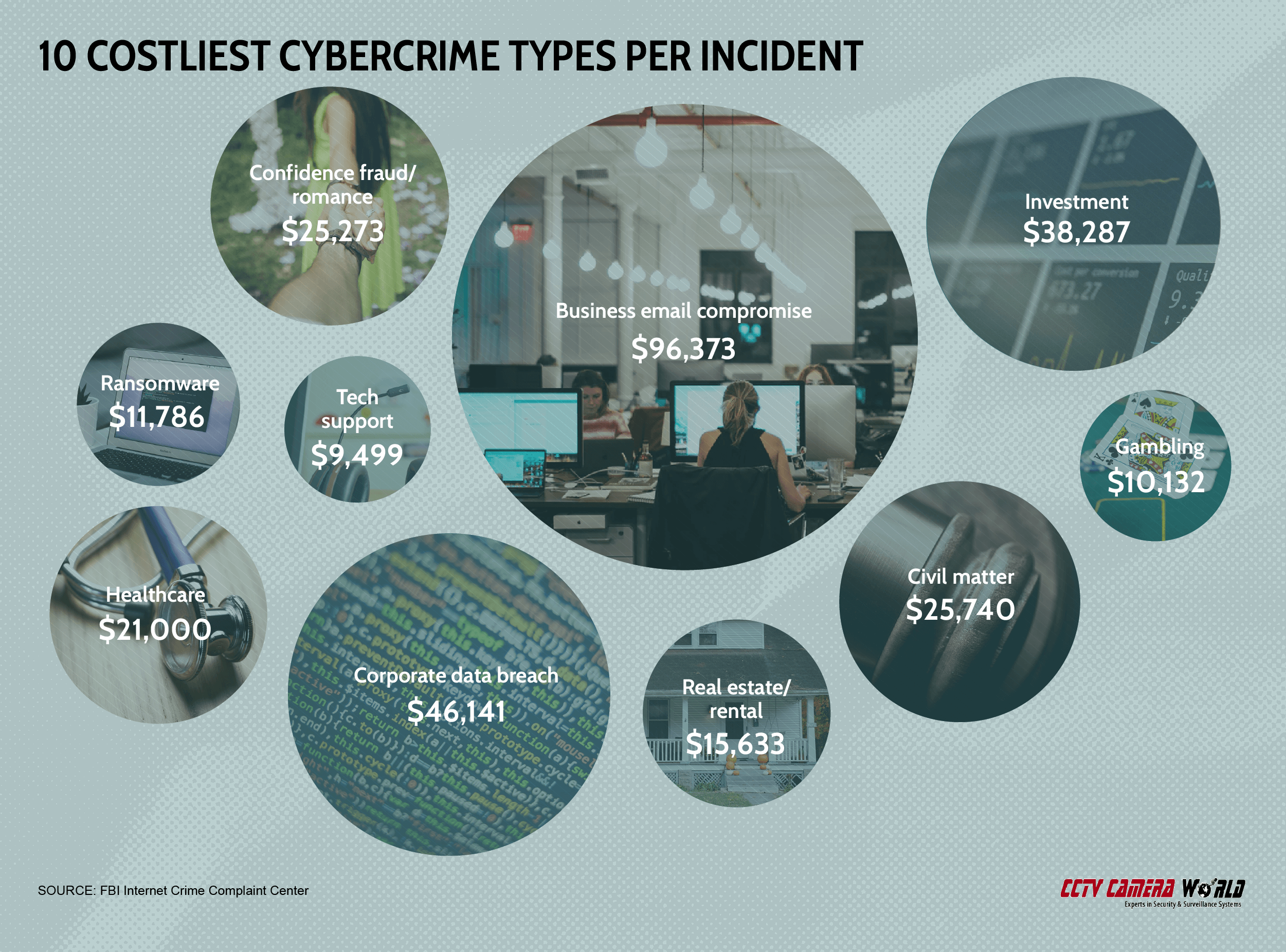
10 costliest cybercrime types per incident
| Business email | $96,373 |
| Corporate data breach | $46,141 |
| Investment | $38,287 |
| Civil matter | $25,740 |
| Confidence fraud/romance | $25,273 |
| Healthcare | $21,000 |
| Real estate/rental | $15,633 |
| Ransomware | $11,786 |
| Gambling | $10,132 |
| Tech support | $9,499 |
Missouri businesses were the biggest victims of BEC attacks in 2020 with an average per-incident loss of just over $375,000. Ohio was second, though its average loss was more than $100,000 less than that of Missouri. The average BEC scam in Montana cost just over $20,000, making them the least valuable.
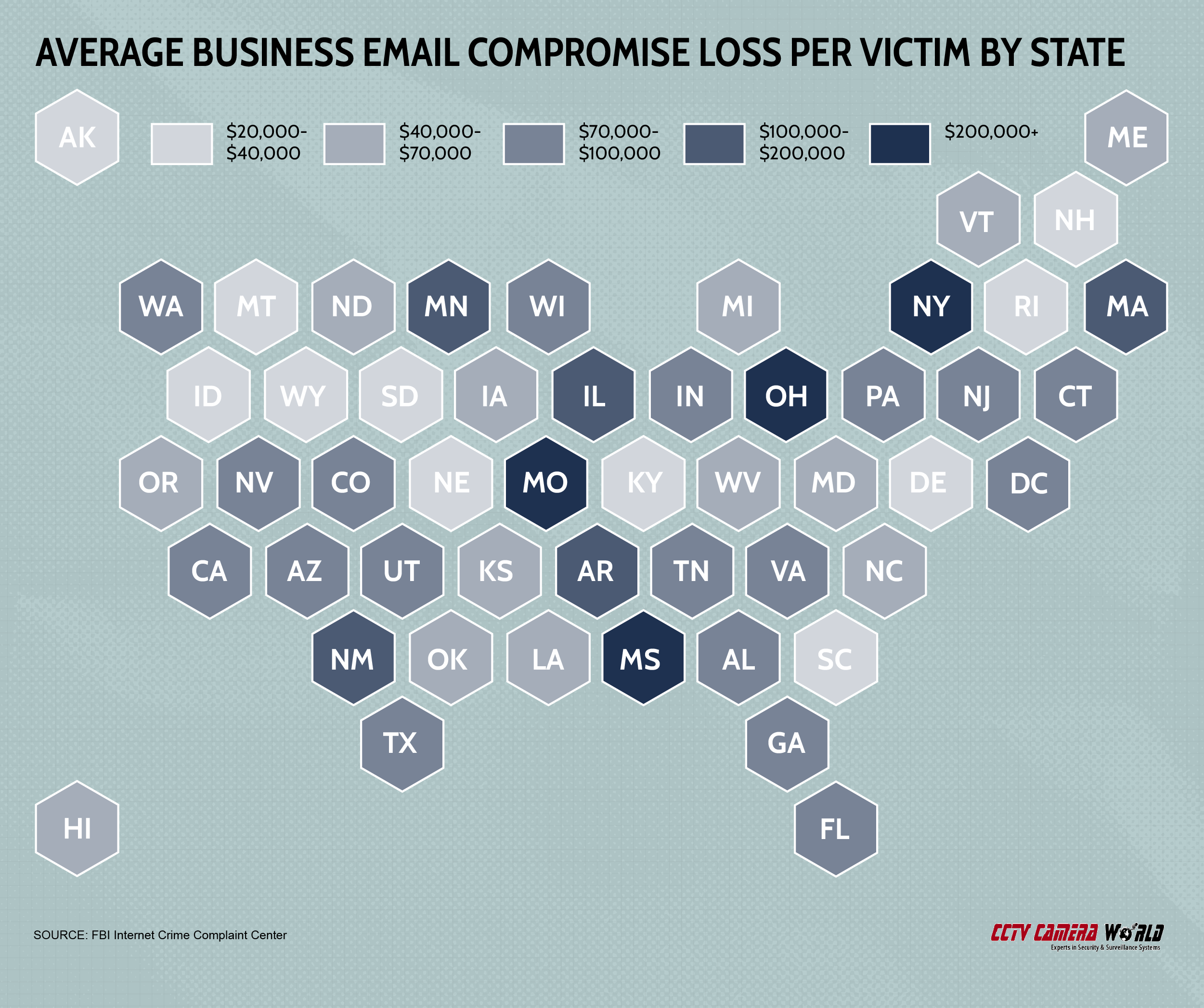
Average business email compromise loss by state
| Missouri | $378,387 |
| Ohio | $267,482 |
| Mississippi | $225,768 |
| New York | $206,418 |
| New Mexico | $122,814 |
| Illinois | $120,822 |
| Arkansas | $111,119 |
| Minnesota | $108,811 |
| Massachusetts | $104,045 |
| Indiana | $99,965 |
| Colorado | $97,964 |
| Nevada | $97,404 |
| New Jersey | $88,138 |
| Connecticut | $85,168 |
| Arizona | $83,735 |
| Tennessee | $83,659 |
| District of Columbia | $83,393 |
| Florida | $83,274 |
| Texas | $81,964 |
| Pennsylvania | $81,514 |
| Virginia | $79,699 |
| Alabama | $76,801 |
| Utah | $75,349 |
| California | $74,939 |
| Georgia | $72,637 |
| Washington | $72,400 |
| Wisconsin | $70,428 |
| Kansas | $63,229 |
| North Dakota | $61,614 |
| North Carolina | $61,054 |
| Hawaii | $58,930 |
| Iowa | $56,370 |
| Louisiana | $53,724 |
| Michigan | $53,590 |
| Maryland | $50,026 |
| Vermont | $46,092 |
| Oklahoma | $45,771 |
| West Virginia | $44,585 |
| Maine | $42,211 |
| Oregon | $41,601 |
| Delaware | $39,423 |
| Idaho | $38,882 |
| South Carolina | $38,209 |
| Nebraska | $37,857 |
| Alaska | $36,938 |
| Wyoming | $34,908 |
| Kentucky | $30,863 |
| Rhode Island | $29,485 |
| South Dakota | $27,069 |
| New Hampshire | $23,527 |
| Montana | $20,371 |
Attacks against home security cameras on the rise
About one in three broadband households in the U.S. has a security system, including those with or without cameras. Camera technology, including indoor and outdoor units and doorbell cameras, are often perceived as the best way to be sure your home and business are safe. But that’s not always the case.
A March 2021 report that a software breach affected hundreds of cameras in Tesla factories and warehouses across the globe was just the latest in a string of incidents shining a light on security flaws in many types of security cameras.
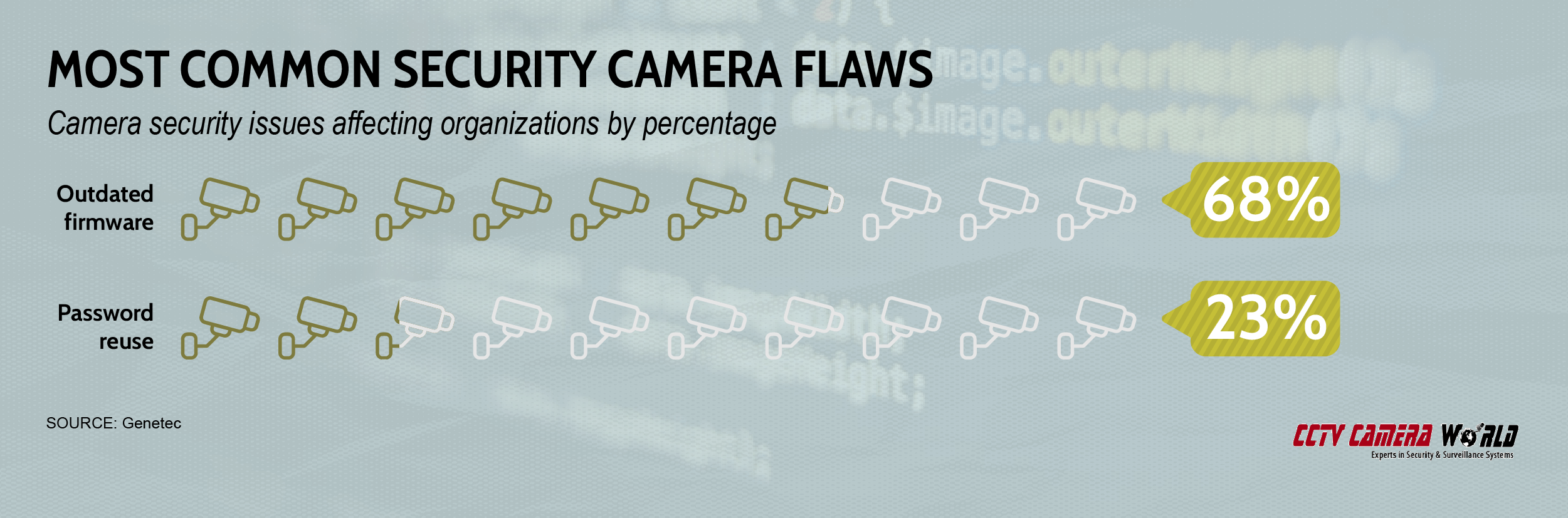
From out-of-date firmware to poor password practices to attacks designed to target internet-connected cameras, even the devices we’re using to make ourselves safe could actually be inviting attacks. Both homes and businesses are at risk, according to data from a recent Genetec survey.
How to protect your home & business
Cybercrime has evolved over the years as fraudsters and criminals have adapted to security measures taken by consumers and cybersecurity providers. And while there’s no doubt they’ll continue to evolve, there are important steps you can take today to reduce your risk of falling victim to a cyberattack:
- Accept that even if you don’t think you are a target, you are. In our modern world, any person or business with an email address, internet connection, or phone number could very well fall prey to criminals and fraudsters. Rid yourself of the “It can’t happen to me” mentality.
- Be aware of any suspicious and (most importantly) unsolicited communication. Email attacks remain the most common, but vishing and smishing attacks are increasingly targeting people via voicemails and SMS text messages. If you’re unsure, it’s best to simply not respond to the communication.
- Don’t overlook physical security. That means never leaving devices unattended, particularly if they contain sensitive information, as well as ensuring the physical premises of your home and business are monitored by security cameras. The stereotype of a cybercriminal is a shadowy figure who only attacks via the internet, but clever digital criminals will use any method they can, and that sometimes includes observing your home or business. And remember that even security cameras can be hacked, so all the same tips and good practices apply to IP cameras, doorbell cameras and indoor/outdoor cameras.
- Practice good mobile device security. If your device has a password or PIN lock setting, ensure it’s active and that only you have the code. Never click on unsolicited links in text or email, and consider data encryption if you will be accessing sensitive financial information. And never use an unsecured WiFi network.
- Make sure all software is up-to-date, not just malware or security programs. Attacks often target random computer programs, and updates can help ensure back-door vulnerabilities are closed. Be sure all firmware is up to date, including that affecting security cameras.
- To avoid falling victim to tech support scams and ransomware attacks, it’s important to maintain a backup of your important data. A free online cloud storage account from Google Drive is a good place to start. Regularly upload data to the account or consider purchasing paid software that does scheduled backups. And make sure the account password is secure and not saved on any computers.
Final thoughts
Cybercriminals are relentless in their efforts to craft increasingly sophisticated schemes aimed at your wallet or your business’s bank accounts. As they evolve, your security measures must adapt to meet the challenge.

