
Stop Hackers From Getting Into Your Security Camera System

As more and more electronics or Internet of Things (IoT) devices require internet access, they become easy targets for hackers and cybercriminals. Security camera systems are no exception to this increased risk. If you want to view your cameras remotely or get alerts, connecting them to the internet exposes them to potential cybersecurity threats.
Within the last few years, several well-known camera brands like Ring, Nest, and SimpliSafe have all been victims of exploits, providing unauthorized access to livestreams and sometimes enslaving devices in botnets. Botnets are networks of compromised devices that are used to launch cyberattacks, including DDoS attacks (overwhelming servers or websites with network traffic), or for use in cryptocurrency mining operations without the owner's knowledge.
Securing your cameras doesn’t have to be complicated. In this guide, we’ll decipher the jargon, educate you on the risks, and provide some practical advice for securing your security cameras and system.
Table of Contents
- Understanding the Cybersecurity Risks of Security Camera Systems
- Secure Your Network
- Strengthen Security Camera System Login Credentials
- Create and Assign User Roles on your Security Camera System
- Update Firmware
- Limit Remote Access & Monitor Activity
- Buy from a Reputable Brand like CCTV Camera World
- Hack Prevention Checklist: Can Your Security Cameras Be Hacked?

Understanding the Cybersecurity Risks of Security Camera Systems
Your level of risk is determined by the specific types of cameras and system setup you have. In an old-school coaxial analog CCTV system composed of cameras that use analog BNC cabling, only the DVR is the digital device in the system that gets connected to the internet, limiting exposure. However, if you use an IP PoE based system, there are several digital or IoT components that are susceptible if placed on computer network; these devices include:
- NVR (network video recorder) that records footage streamed over the network or from any cameras that are directly connected
- PoE cameras that capture and send footage back to the NVR either over a network or directly to the NVR
- PoE Switch that is frequently used in commercial surveillance systems to provide data and power to a large number of cameras
The recorder and cameras of a system are targets of attacks for several reasons:
- Typically, they maintain a constant internet connection.
- Often have default passwords that are easily researched.
- Hacking IP cameras for use in botnets is ideal due to their prevalent use worldwide.
- Video feeds could also give criminals insights for planning burglaries or stalking individuals.
For example, prior to 2017, there was an exploit that affected a vast number of coaxial DVRs because they used a default back-end password. To take advantage of this exploit, hackers set up computer bots that automatically searched the internet for vulnerable DVRs. These bots would then access the system using the default system password, lower the brightness of the cameras to a completely black state, and change the channel names, causing confusion. More nefarious actors who gained access to DVRs reviewed footage to make more personalized changes to freak owners out.
One of the easiest ways to tell if your camera is hacked is by checking for unexpected settings changes that you didn’t make. If you notice altered passwords, renamed cameras, disabled security features, or unfamiliar remote access settings, it could be a sign that someone has gained unauthorized access.
And that’s just one example of an exploit that led to a widespread security camera system hack. Exploits often take advantage of the following common security vulnerabilities:
- Open ports
- Compromised networks
- Default passwords
- Outdated firmware
- Cloud storage risks
So, what are some things you can do to secure your surveillance system from hackers?
Below, we list some simple yet important steps you can take to reduce the risk of cyber threats to your security system

1) Secure Your Network
Connecting your network surveillance cameras and recorder to the internet will cause them to be at greater risk than if they were not connected. However, there are several ways you can have them connected to the internet and add additional barriers to prevent unauthorized access and mitigate attacks from spreading.
Isolate Your Camera Network
One of the most effective ways to protect a security camera system from cyber threats is network segmentation, also known as network isolation. This strategy involves creating a separate network for security cameras so they don’t share the same connection as your computers, printers, or other devices. Putting cameras in their own isolated network limits the risk of threats spreading from one compromised device to another.
Using a technology known as VLANs is one of the most common ways to isolate your cameras on a network. VLANs, short for Virtual Local Area Networks, are digitally segmented networks that use a different IP address scheme than the main network.
To set up a VLAN, you will need a router or managed PoE switch that supports it. For example, your main network may use a standard scheme of 192.168.1.xxx, and the router or switch will allow you to create a virtual network that uses a 192.168.2.xxx scheme. This segmentation ensures that cameras remain inaccessible from other networked devices and the outside world unless explicitly allowed by firewall rules.
You might wonder how you can still access your isolated security cameras remotely. To maintain security without losing remote access, purchase an NVR with two network ports such as 64 channel NVR. One port connects to the main network with internet access, while the second connects to the VLAN for direct communication with the cameras. With proper firewall rules, only authorized users and devices will be able to connect to the NVR, ensuring that remote access is secure.

Avoid Port Forwarding
In the past, port forwarding was the only method for remotely accessing CCTV camera systems. It worked by creating rules in a router or modem—often referred to as “hole punching”— that allow traffic from the internet to pass through the router into the DVR.
However, port forwarding is very insecure because it exposes the system directly to the internet, with only the username and password as protection. This vulnerability played a major role in the 2017 security camera hack, where automated bots scanned the internet for open systems and exploited default credentials to gain unauthorized access.
Thankfully, modern solutions such as VPN and P2P technologies offer enhanced security for remote access security cameras. These technologies significantly reduce the risk of cyber threats by encrypting data and prevent direct exposure of your camera system to the internet. However, this added security comes with a trade-off: because VPN and P2P services use intermediary servers to route your connection, there can be a slight delay in response time compared to the near-instant connectivity provided by port forwarding.
The only benefit of configuring port forwarding on your router for remote viewing is the fast response times it provides. Port forwarding doesn't involve any servers in the middle; it is more of a direct connection from the viewing device, like your smartphone, to the DVR, with only networking switching equipment across the internet being in between.
If you're an advanced user you can implement an IP address whitelist rule for trusted IP addresses across the internet that should be allowed remote access to your system. All of the professional security DVR that we carry here at CCTV Camera World have this option. If your recorder doesn't, you can invest in a good professional firewall such as a Cisco or Firewalla device.
If you're more concerned about robust cybersecurity than achieving lightning-fast response times, modern VPN and P2P solutions offer a far safer alternative for remote access. In today's ever-evolving digital landscape, this extra layer of protection is essential. By moving away from the insecure port forwarding method, you'll significantly reduce the risk of unauthorized breaches and better safeguard your surveillance equipment.
2) Strengthen Security Camera System Login Credentials

This step might seem obvious, but default passwords remain one of the biggest risks for security camera system hacking. The good news is that most modern systems require password changes during setup, reducing the risk. However, cheaper security cameras from big-box retailers may still ship with factory-set credentials—many of which are easily found online with a quick Google search. There are many more reasons why you should not buy cheap security cameras.
Every system at CCTV Camera World comes with a pre-initialized password that differs from the factory default, providing you with an immediate security advantage. Still, regularly updating your passwords, usually every 6 to 12 months, remains one of the best practices for keeping your system secure. If you share access with your family or friends, keep separate usernames and passwords for them so that you can remove or turn off their access when you want to.
In the video below, we show how to modify the password for the Admin user, or any other user on one of our DVR or NVR recorders. The video guide uses the display output to a HDMI monitor from the recorder. You would carry out these steps by being in front of the recorder. If you would like to administer these privileges over the web interface of the recorders, please continue reading below.

Our professional security systems allow administration over the web interface of the recorder as well. Below we show the steps you would need to take to create user accounts using Internet Explorer.
How to modify the password for the Admin User
- Using IE11 navigate to the IP address of your NVR or DVR and log in as the "admin" user. The default password is written on a label on the top of the recorder.
- Select the “Setup” tab at the top of the screen.
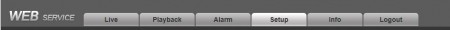
- Now select "System" > “Account” from the left side menu
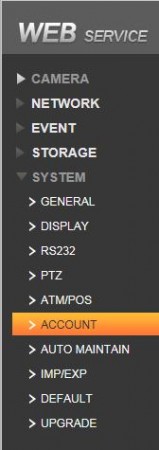
- Select "Modify" on the admin account then check the "Modify Password" box.
- Change your admin password to a complex password without any spaces. Don't forget to keep the password in a safe place!
3) Create and Assign User Roles on your Security Camera System
Another important security tip we recommend is to create secondary user accounts other than the main Admin user for daily use for yourself. If you have other users who you would like to allow access, create unique and separate accounts for those users.
In the video below, we use one of our Network video recorders to demonstrate how you can set up different user accounts with unique permission privileges. The original "Admin" username would remain with Admin level privileges. For new users you create, we recommend assigning permission from the "User" group which has limited privileges, which reduces the potential for disruption from a hack.
The video guide uses the display output to a HDMI monitor from the recorder. You would carry out these steps by being in front of the recorder. If you would like to administer these privileges over the web interface of the recorders, please continue reading below.

Our professional camera systems allow easy administration over the web interface of the recorder as well. In the steps mentioned below, we show how to create user accounts using Internet Explorer.
After continuing steps in the section above that show how to access the web interface, create a new user by selecting the "Add user" button at the bottom. These users will be generic rights templates for the users that will have access to monitor, playback, record etc on the recorder.
You can create more than one user if you have roles that need to be filled separately. (ie: Someone who monitors live feeds vs. someone who views old footage).
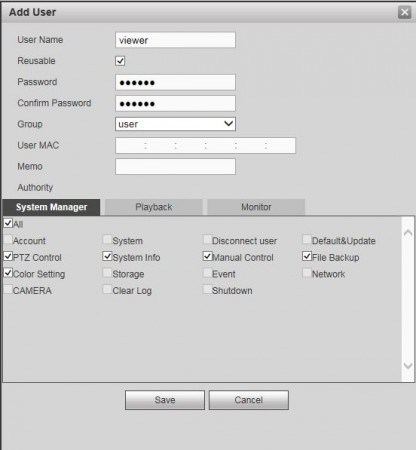
- Create a username
- Select Reusable (very important)
- Create a complex password without any spaces
- Select "User" from the group drop-down box
- Adjust System Manager, Playback, and Monitor privileges as needed
4) Update Firmware
Staying up to date with firmware updates of IoT devices is key as they usually address newly discovered exploits among other things such as feature improvement. Keeping your recorder and IP security camera firmware up-to-date will make sure that they have the latest security patches. To go back to our example, the 2017 hack was quickly mitigated by the manufacturer releasing a firmware update that removed the backdoor admin account. Just like updating passwords, we recommend that you check for firmware updates every 6 to 12 months. To check for and request a firmware update for your device from CCTV Camera World, please send a support request and have the following information ready:
- Order Number
- Model Number
- Picture of the current firmware version—found in the System Information settings of the device.
Keeping up with firmware updates is a straightforward measure that further safeguards your security system against cyber threats. With automatic firmware updates available on Security Cameras Inc and AvaEye branded products, you can enjoy enhanced security and peace of mind.
5) Limit Remote Access & Monitor Activity
The most effective way to secure your home or business security camera system is by limiting or disabling remote access entirely. If your NVR or DVR is disconnected from your router or modem, it can only be accessed on-site, eliminating the risk of remote hacking. While this may not be the most convenient option, it is the most foolproof way to prevent unauthorized access.
For those who need remote viewing, we recommend regularly monitoring access logs to track who is logging in and when. The Avalonix Premium Series IP cameras and recorders automatically log user activity, allowing you to review login timestamps and access attempts. These logs can typically be found in your device’s system settings.
6) Buy from a Reputable Brand like CCTV Camera World
When selecting a security camera system, it's important to do your homework. Before making a purchase from a brand, check for news of any current vulnerabilities or data breaches related to that brand. If a company has recurring security difficulties, you should look elsewhere.
Every product we sell undergoes rigorous testing before it even reaches our website. We constantly upgrade the firmware on our devices to address vulnerabilities and improve performance. With us, you're not only purchasing a product; you're also investing in a reliable partner who is committed to keeping your surveillance secure.
Hack Prevention Checklist: Can Your Security Cameras Be Hacked?
Modern security cameras and recorders are designed with stronger protections than ever before, making hacking them more difficult. However, no system is completely secure—new vulnerabilities can be discovered, and hackers often develop automated bots to exploit them.
This quick checklist will help you verify your system’s security and ensure that your cameras are protected against potential threats.
- Change Default Passwords — Ensure all default credentials have been updated to strong, unique passwords.
- Check for Unauthorized Settings Changes — If you notice invalid passwords, renamed devices, blank camera channels, image settings changes, or disabled security settings, it may be a sign of a breach.
- Keep Firmware Updated — Check for firmware updates every 6 months to a year to patch known security vulnerabilities.
- Disable Port Forwarding — Avoid exposing your cameras directly to the internet; use a P2P connection instead.
- Review Access Logs — Regularly monitor who is logging in to detect suspicious activity.
- Isolate Cameras on a VLAN — Keep and PoE IP cameras on a separate network from other devices to prevent access to your main network.
- Set Up a Firewall — Restrict access to cameras from specific trusted IP addresses and block unnecessary connections.
- Scan for Open Ports — Use a network scanner like GRC’s Shields Up! port scanner to check if your system has exposed ports that could be exploited.
- Test Remote Access Security — Try logging in from an external device to confirm your system is properly secured.
