
Physical Security Guide: Controls, Measures, and Planning for Homes and Businesses

Although we specialize in surveillance here at CCTV Camera World, it's just one aspect of home or business security. Physical security plays a vital role in developing a comprehensive strategy to safeguard your family, guests, customers, and employees.
In today’s world of rapidly advancing technology, physical threats aren’t just about break-ins or vandalism; they can lead to identity theft, cybersecurity breaches, data loss, and other disruptions. Whether you own a home or manage a retail store, warehouse, or office building, this guide will walk you through what an effective physical security strategy looks like and how to build a strong, layered defense.
Table of Contents
- What is Physical Security?
- Common Physical Security Threats, Vulnerabilities, and Risks
- Physical Security Measures and Control Technology
- The 5 Pillars of Physical Security
- How to Assess Risks at Your Home or Business
- Camera Placement and Surveillance Best Practices
- Real-World Examples of Physical Security Challenges
- Final Thoughts on Physical Security
- Frequently Asked Questions
What is Physical Security?
Physical security refers to strategies designed to limit exposure to risk, liability, and crime from individuals who aren't permitted to access the property. These measures can include rules, standard operating procedures, electronic systems, devices, and even physical barriers.
Ignoring or failing to implement proper security protocols can lead to serious consequences, from unauthorized access and break-ins to theft and vandalism. Installing the right security equipment and making sure you, your family, or your employees follow those protocols doesn't just provide peace of mind; it ensures you're prepared for whatever comes your way.
Common Physical Security Threats, Vulnerabilities, and Risks
Every property has weaknesses, even if they’re not obvious at first glance. Before you can build an effective security plan, it helps to understand the most common threats and how they show up in day-to-day situations. Many of these aren’t dramatic or unusual; they come from simple gaps that criminals look for and exploit.
- Burglaries and break-ins: forced entry through weak doors, unsecured windows, or hidden access points.
- Theft and vandalism: outdoor equipment, tools, vehicles, catalytic converters, and anything left in plain sight.
- Tailgating and unauthorized entry: people slipping in behind staff, delivery drivers, or tenants.
- Insider threats: employees propping doors open, misusing credentials, or accessing restricted areas.
- Loitering and casing: individuals hanging around entrances, parking lots, or alleys while scouting your routines.
- Workplace disputes: confrontations that escalate due to lack of visibility or access control.
- Environmental risks: fire, flooding, storm damage, and power outages that suddenly take down cameras or lighting.
- Cyber-physical overlap: stolen recorders, exposed network ports, weak passwords, and unpatched devices.
None of these threats require advanced tools or planning. Most occur because of routine habits, dark corners, or equipment that no one checks anymore. Recognizing these weak points early makes the rest of your security plan far easier to build.
Physical Security Measures and Control Technology
Physical security goes way beyond a few cameras and a decent lock. It’s really about how the property is laid out, how people move through it, what’s protected, and what’s easy to get to. Before getting into the five pillars, it helps to look at the basic pieces that show up in almost every solid security setup.
- Property layout and visibility: removing blind spots, improving sight lines, and using lighting to reduce hiding places.
- Access control: doors, locks, keypads, badges, door sensors, and policies that keep restricted areas closed off.
- Perimeter protection: fencing, gates, bollards, or anything else that slows down or discourages someone from getting too close.
- Intrusion detection: cameras with smart analytics, door contacts, glass-break sensors, and alarms that trigger when something isn’t right.
- Environmental and infrastructure protection: lighting, clear signage, and secure storage areas for tools, equipment, or anything valuable.
- Surveillance systems: cameras, NVRs or DVRs, remote access apps, and features that help you spot real motion instead of shadows or headlights.
- Staff training and procedures: clear rules about locking doors, reporting suspicious behavior, and using security equipment correctly.
These pieces are the foundation of any good plan. The five pillars (Deterrence, Detection, Delay, Response, and Recovery) help organize these measures into a layered defense that protects people and property from multiple angles.
The 5 Pillars of Physical Security
Now that we've defined physical security, we can dive into the specifics. To start, we’ll outline the five pillars of physical security to gain an understanding of the foundation for a successful security plan. These pillars can be thought of as preventative and mitigation measures. Preventative measures aim to deter or stop a threat from becoming an issue before something happens. Mitigation measures are taken to reduce the damage a threat can cause if an event or breach occurs.
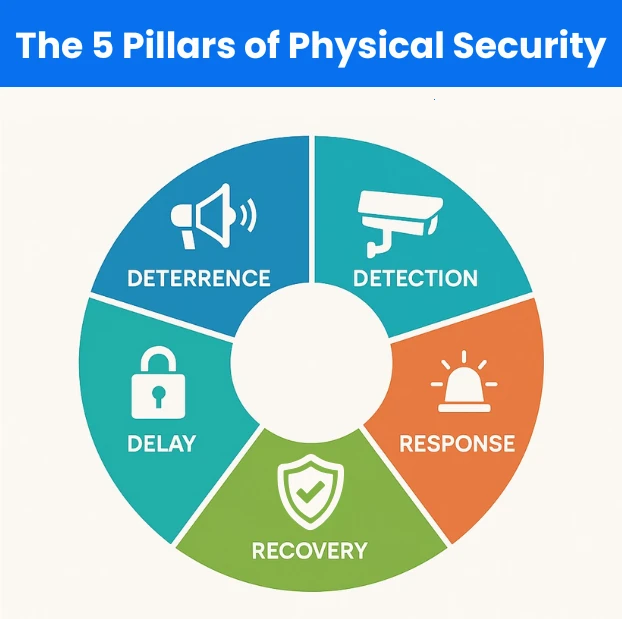
Deterrence
One of the first lines of defense is deterrence, which is a preventative measure that includes signage, clearly visible cameras, and ample lighting. Having an abundance of deterrents will tell potential attackers that your building is not an easy target.
CCTV Camera World’s Active Deterrence cameras are a perfect fit for deterrence strategies. Cameras with deterrent features have built-in LEDs and loudspeakers that are activated manually or automatically via Smart Detection rules to scare off intruders or make announcements to wandering pedestrians. Our customers have had success using these cameras in various locations, including their garages and storefronts.

Detection
Detection is another layer of protection that’s useful for both prevention and mitigation. Detection is achieved through surveillance cameras, motion detectors, sensors, alarms, and other electronic devices that trigger when areas are breached, windows are broken, or doors are opened.
All cameras from CCTV Camera World include some form of motion detection, and several IP cameras have Smart Detection features. Smart Detection uses AI-powered algorithms that watch the video feed for people or cars to make detection more accurate. Some of these detection methods, such as digital tripwire and intrusion detection, allow users to set customized rules to protect specific areas or objects within the camera’s view. Smart Motion Detection (SMD) is like old-school motion detection, but instead of solely triggering based on changes in pixels, SMD enhances this process by analyzing the video feed for the presence of humans and vehicles.

Delay
Delay is in the mitigation category, as any devices or methods that fall under the delay pillar are used to slow the situation down, whether it’s an intruder, attacker, or other threat. Delays include locks, doors, fences, safes, and reinforced or guarded entry points, to name a few. Delay mitigation tools and strategies often also cover the detection pillar through integrated sensors.

Modern delay devices are able to be combined with security camera recorders using a built-in alarm panel to send alerts through the remote viewing apps and PC software. Quick and reliable alerts are part of the next pillar, “response,” and mean you or your security staff will be notified when your delays are approached or breached to make quick decisions and contact authorities if necessary.
Response
The term "response" describes your ability to act swiftly and efficiently after detecting a threat. Whether it’s a break-in, loitering, or some other unauthorized access, having a plan in place ensures threats don’t go unanswered. Response plans include real-time alerts, remote camera access, and alarm-activated lights and sirens.
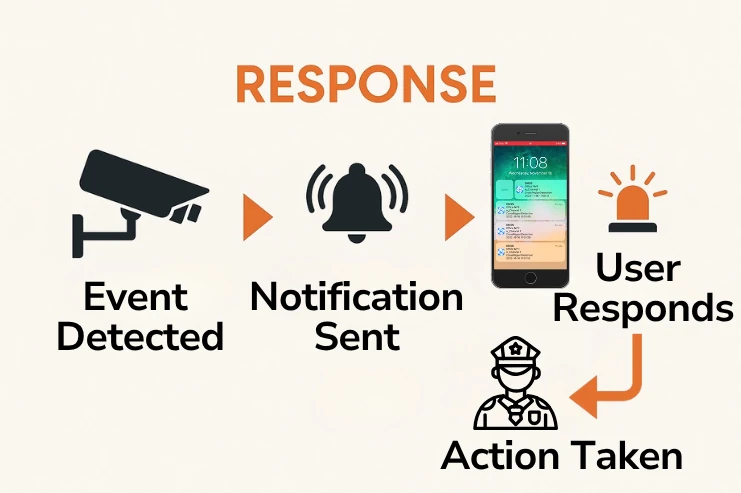
CCTV Camera World offers security camera systems that facilitate rapid responses through push notifications, live viewing, and remote control of deterrent features in cameras. Many of our customers use these tools to monitor and prevent suspicious activity before damage occurs, whether it’s speaking through two-way audio speakers or reaching out to authorities with video evidence in hand.
Recovery
Recovery focuses on what happens after an incident has occurred and can be thought of as a mitigation strategy. This pillar is about having procedures in place to investigate, document, and bounce back from a security breach, whether it’s theft, vandalism, or trespassing.
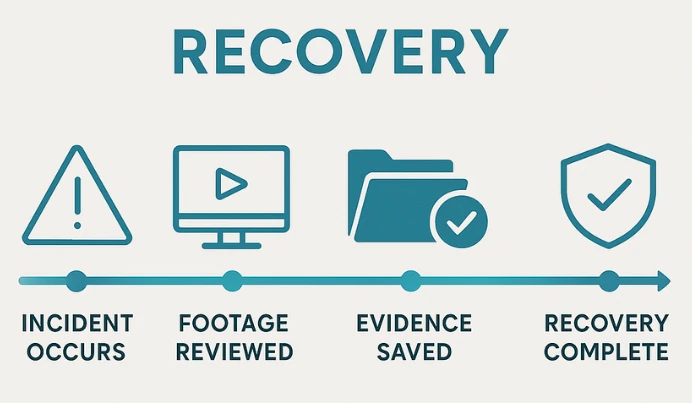
With a reliable NVR or DVR system and proper camera placement, you’ll have clear, timestamped video evidence that can be used to identify suspects, file insurance claims, or support police investigations. Many of our customers have utilized recorded footage to retrieve stolen items and collect evidence for insurance claims. Backing up storage, purchasing large recorder configurations with ample storage for long retention times, and regular maintenance are key to staying prepared.
Physical Security Planning: How to Assess Risks at Your Home or Business
With the pillars of physical security defined, you can begin your journey to identify your specific security risks and address them with a plan. A useful place to start is to conduct a thorough walkthrough of your property using a pen and some paper or the notes app on your phone.
Before buying equipment or making upgrades, it’s important to understand how people move around your property, where the weak spots are, and which areas would cause the most damage if something went wrong. The following steps will help you evaluate risks in a structured way so you can address the issues that matter most.
Start With Access Points
First, you’ll want to identify all of the access points, including front doors, side doors, garage bays, emergency exits, and windows.
- Make a list of all access points to the interior of your building.
- Note which entry points are already secured, monitored, or alarmed.
- Note which access points have weak points. For example, weak hollow-core doors, easily breakable or dislodged windows, and exits that people might leave propped open are all entry points with vulnerabilities.
Evaluate Surveillance Coverage
Another beneficial step you can accomplish while you’re noting access points is to also evaluate your security camera coverage.
If you don’t have security cameras, now may be a good time to survey your property and estimate how many you need. If you already have cameras, it may be time to start thinking about upgrading them to benefit from the latest advancements in video quality and Smart Detection features.
- Compile a comprehensive list of all your current cameras.
- Search for blind spots in areas like hallways, stairwells, corners, and loading docks or garages.
- Double-check to ensure that your cameras are aimed properly.
- Assess the quality of recorded footage from nighttime to verify it’s useful.
Check Lighting and Visibility
It's important to conduct another walkthrough at night to determine if the darkness increases any vulnerabilities. TheSleepJudge's data collection and analysis showed that, despite a 10% increase in crime during the day, violent crime is more prevalent at night. Parking lots at night are also common targets, and they pose liability issues if the lighting is poor.
Lighting also plays a significant role in surveillance and deterrence. Ensuring that your cameras have clear, well-lit, and unobstructed views at night is crucial for gathering evidence. Well-lit homes, businesses, or individuals are less likely to become targets for criminals.
- Check lighting around entrances, parking areas, and alleys for dark and poorly lit areas.
- Note down any broken, flickering, or dead exterior and streetlights.
- Determine if rooms with valuables are visible through windows, like bedrooms, offices, or server rooms.
Review Physical Barriers
Checking physical barriers that are already in place or considering adding new barriers is a solid next step. When evaluating the physical barriers, ask yourself, “Would it take more than 30 seconds to break into my most sensitive area?”
- Inspect fencing, gates, bollards, and locked storage areas.
- Look for locations where individuals can engage in climbing or parkour.
- Confirm that restricted zones and storage areas for valuables are separated and have locks.
Assess Protocols and Human Habits
Unfortunately, humans are the number one risk when it comes to physical and cybersecurity. Developing and following strict procedures, protocols, and rules will reduce the effect human error has on your security plan. When coming up with your security protocols, ask yourself the following questions:
- Are doors left unlocked during business hours?
- Do employees prop open exits or leave sensitive areas unsupervised?
- Are visitor check-ins enforced, and do staff know who’s authorized?
- Is there a clear procedure for reporting suspicious behavior?
- Do all members of your household, especially kids or teens, know when and how to lock up securely and activate your alarm system?
- Do you have a plan for how your family should respond if someone tries to enter unexpectedly?
Develop and Evaluate your Monitoring and Response Plans
The second part of the protocol assessment should relate to monitoring and responses. To evaluate your response plans, consider the following questions:
- Who monitors the cameras? Do they monitor the cameras in real time or only after incidents?
- Are there alerts for off-hours motion?
- Is the footage backed up on-site to another recorder, a file server, SD cards in the cameras, or a combination of the three?
- Is there a clear chain of communication and command if something suspicious happens?
- Are there set thresholds before authorities are involved?
- Is there a defined process for gathering and documenting evidence?
Document Your Findings and Enact Changes
Now that you’ve assessed your property’s security, you’ll want to document your findings and have discussions about plans, upgrades, and protocols.
- Make a checklist of security flaws, camera locations, lighting issues, and other problems that need to be addressed.
- Take photos during the walkthroughs to create a plan of action for addressing these issues.
- Ensure your equipment, plans, and protocols are up to date by scheduling assessments and walkthroughs every 6–12 months and after every incident.
Camera Placement and Surveillance Best Practices
Having a reliable security camera system is one of the best ways to secure your home or business. Cameras allow you to monitor activity in real time and review footage in the event of an incident. But if you don’t work with surveillance systems regularly, knowing where to place cameras and which types to use can feel overwhelming.
At CCTV Camera World, we’ve helped thousands of customers choose the right cameras the first time. The following tips will help you map your layout, identify critical zones, and select the right equipment to build an effective system.
Start with a Sitemap Overview
Whenever you start planning to install or upgrade a security camera system, you will want to start by plotting where cameras should go and how they're aimed to maximize coverage. Making an overview is one of the best ways to decide how many cameras you need and where to point them. We recommend using Google Maps, but if you have blueprints or a property map from your local government, that may work better.
Create a Sitemap using Google Maps
- Open Google Maps and search your property’s address.
- Take a screenshot of your building or lot using your computer’s Snipping Tool.
- Open the image in Microsoft Paint or a similar program.
- Use shapes or markers to label areas you want to cover. Refer to the list in the section below for some examples.
Identify Critical Zones
The following lists are useful references for placing cameras on your sitemap. These locations are some of the most critical areas to protect with cameras. Consider the perspective of an intruder; where would you enter?
For businesses:
- Entry and Exit Points
- Parking Lots/Garages
- Stairwells
- Cash Registers
- Server Rooms
- Lobbies
- Stockroom/Warehouse
For homes:
- Front/Back Door
- Garage
- Driveway
- Yard
- Fence line
- First-floor windows
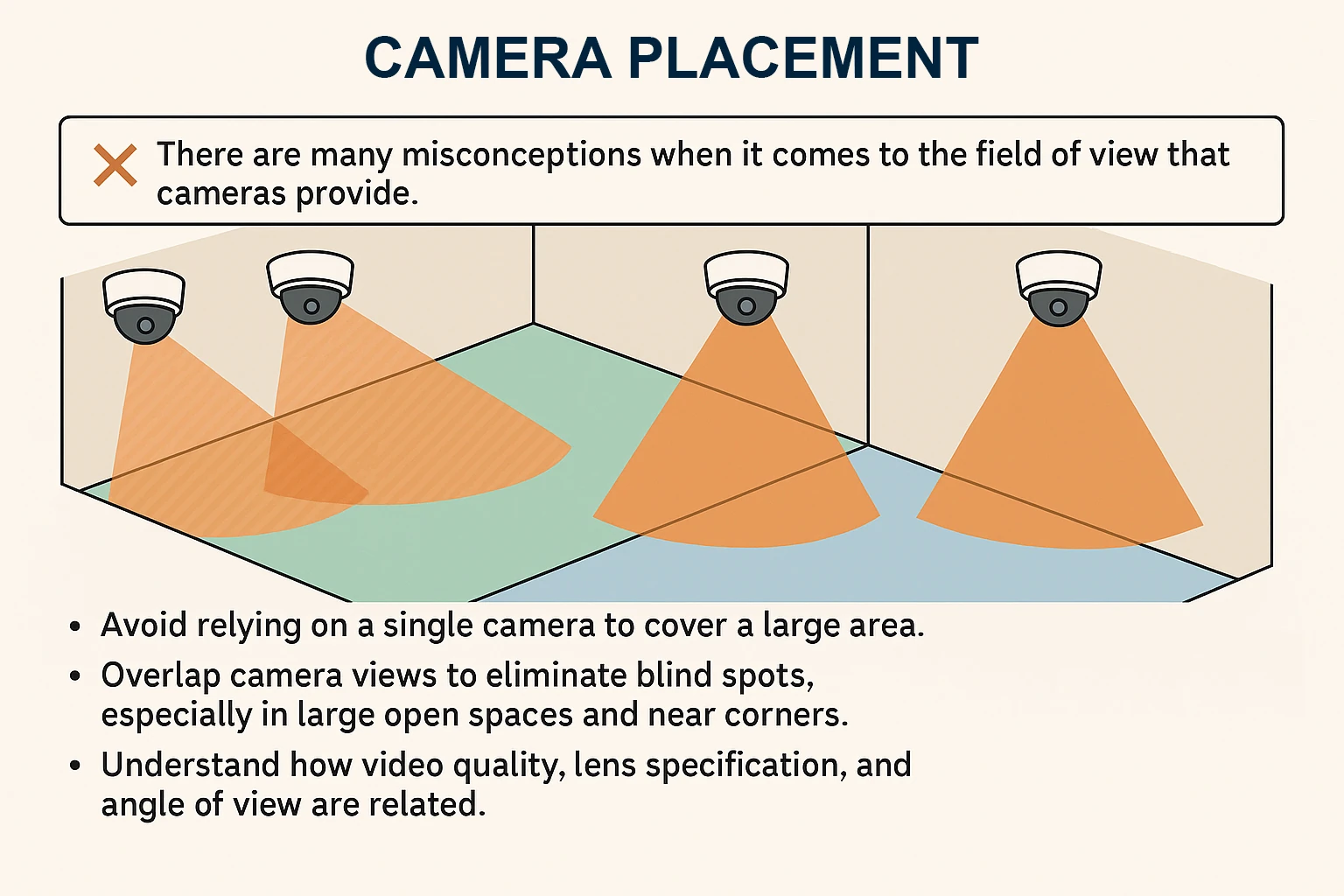
Estimate Fields of View and Aim for Overlap
There are many misconceptions when it comes to the field (or angle) of view that cameras can see. People often assume they can use multiple wide-angle cameras and consider it a successful solution. Unfortunately, due to how optics work, wide-angle fixed-lens cameras are excellent for general detail but are not always the best choice for detail at a distance.
Keep the following in mind when selecting cameras:
- Avoid relying on a single camera to cover a large area.
- Overlap camera views to eliminate blind spots, especially in large open spaces and near corners.
- Understand how video quality, lens specification, and angle of view are related. 2.8 mm lenses capture a wider scene, while 3.6 mm cameras are more zoomed in for better detail.
Choose the Right Camera for the Job
Another common assumption is that all cameras can capture plates, see faces at a reasonable distance, and have “color” night vision. While we wish this assumption were true, it’s simply not. While standard fixed-lens cameras with no extra features excel in general surveillance, they frequently lack the essential features for specific applications. Mixing camera types provides overall coverage and critical detail where needed.
Real example: why a regular camera can’t read plates at night

This screenshot is from one of our own 4K cameras. The scene is bright enough to see a person walking and a van pulling in, but notice what’s missing — there’s no usable face detail and the license plate is completely blown out. That isn’t a glitch or a bad camera. It’s just how general-purpose cameras behave at night, especially when headlights or distance get involved.
If you actually need plate numbers after dark or while a vehicle is moving, you have to use a dedicated license plate capture camera. Those cameras are built for the job and only work when they’re installed at the right angle and the right distance. Without that setup, even the best 4K camera
Even the best security camera can’t do its job if it’s blinded by sunlight and reflections or blocked by a tree branch. Poor lighting and unanticipated obstructions are some of the most common reasons footage ends up being unusable. Whether you're dealing with glare, shadows, or overgrown landscaping, be mindful of what your cameras see both during the day and at night. Proper placement isn't just about direction; it's also about height, angle, and location. Mounting too high can make the view useless, and mounting too low makes the camera an accessible target for vandalism or tampering. Getting this right ensures your cameras capture useful, detailed footage without leaving gaps. A PoE camera system is only useful if it records when something happens and you can access the footage. Planning out your recording schedules, storage setup, and alert preferences is critical for convenience and effectiveness. Every property is different, but most security problems fall into a few predictable patterns. Here are common scenarios that highlight how small vulnerabilities turn into real incidents: These situations aren’t rare, they’re the exact issues people call us about daily. Each example reinforces the same point: clear lines of sight, proper lighting, and cameras placed with intention prevent most issues before they escalate. Physical security is not about gadgets or fear; it is about prevention and preparation. Whether you manage a warehouse, run a small business, or just want your family to feel safe at home, building a layered defense keeps problems small and predictable. Walk your property, search for weak spots, and fix what you can see right away. A sturdy lock, bright lights, and a clear camera view will do more for safety than anything else you can buy. The goal is not perfection; instead, it is awareness. Every small change helps. Locking a gate, trimming a bush, or adjusting a camera might not seem like much, but together they make a big difference. When something goes wrong, having clear video and a plan means you can handle it without panic. We at CCTV Camera World think that physical security should be practical, affordable, and based on everyday needs. Our systems include reliable hardware, smart detection, and easy setup, so you don't have to worry about maintenance. You can focus on your business or keep your house safe. If you want to secure your property, check out our professional surveillance systems. You'll discover how easy it is to get professional-grade protection without paying monthly fees. Physical security refers to the measures used to protect people, property, and assets from physical threats like theft, vandalism, or unauthorized access. It combines barriers, surveillance systems, and security protocols to prevent and respond to incidents effectively. Learn more in our overview of physical security. The five pillars of physical security are Deterrence, Detection, Delay, Response, and Recovery. Together, they create a layered approach that helps prevent, identify, and respond to threats effectively. Learn more in our Five Pillars of Physical Security section. Deterrence discourages crime before it happens using visible cameras, lighting, and warning signage. Detection identifies threats in progress using motion sensors, alarms, and AI-powered Smart Detection cameras. Smart Detection cameras use AI algorithms to recognize people and vehicles, reducing false alerts from movement like leaves or shadows. This allows you to respond only to real threats, not environmental motion. Delay barriers include fences, reinforced doors, locks, and safes. Basically anything that slows down an intruder’s progress can be considered a barrier. These systems can also integrate with your security camera recorder to send alerts when breached. Response is how quickly you act after a threat is detected. It includes push notifications, live video access, sirens, and two-way audio to warn intruders or alert authorities. See our section on Response planning for setup ideas. Recovery focuses on reviewing footage, documenting incidents, and restoring normal operations after a breach. Maintaining reliable NVR/DVR backups ensures you can retrieve evidence or support insurance claims. Start by walking through your property and noting all access points, lighting conditions, and existing camera coverage. Identify weak spots like poorly lit areas or unmonitored entrances, then use our Security Walkthrough section to document improvements. Position cameras at 8-10 feet high, overlapping their fields of view to avoid blind spots. Avoid direct sunlight and reflections, and keep trees or signs from blocking your line of sight. Explore our Camera Placement section for diagrams and examples. Use a mix of cameras for comprehensive coverage: More details are in our Camera Type Comparison section. For homes, aim to keep footage for 7-14 days. For businesses, retain at least 30 days for incident review and compliance purposes. Use our NVR and DVR Storage Calculator to estimate required hard-drive capacity. Lighting impacts both deterrence and image clarity. Ensure entrances and parking areas are well-lit, avoid glare into the lens, and use cameras with built-in white-light LEDs where ambient light is low. Re-evaluate your physical security setup every 6-12 months or after any security incident. Update camera placement, lighting, and staff or family procedures as needed. Physical breaches can expose sensitive data, and cyberattacks can disable physical devices. Combining both defenses ensures complete protection of your property and digital assets. Install visible deterrence cameras, improve outdoor lighting, and create a response plan with real-time alerts to your smartphone. Even a few simple steps can reduce risk dramatically.
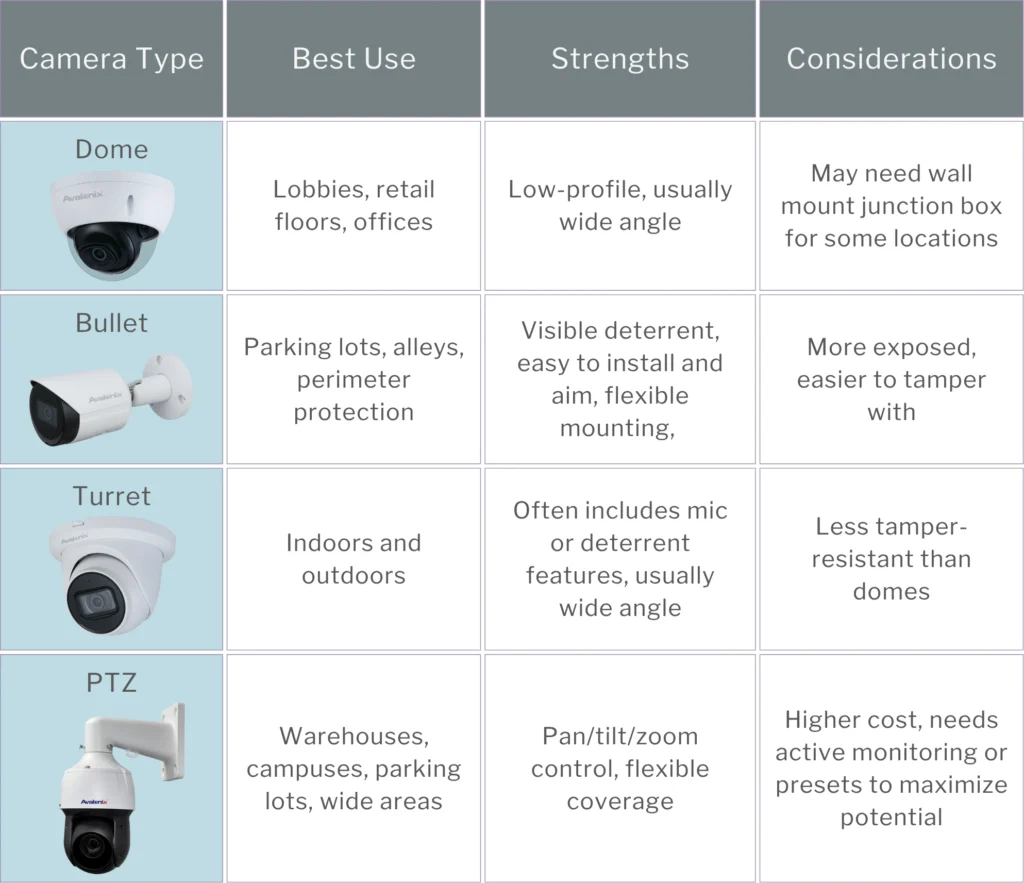
Consider upgrading to specialized models:
Don’t Forget About Lighting and Obstructions
Keep these tips in mind:
Mounting Tips for Best Performance
Mounting best practices:

Plan for Recording, Alerts & Review
Keep the following in mind:
Real-World Examples of Physical Security Challenges
Final thoughts on physical security
Frequently Asked Questions: Physical Security for Homes and Businesses
What is physical security? What are the five pillars of physical security? What’s the difference between deterrence and detection? How do smart security cameras improve detection? What are examples of delay barriers in physical security? What does "response" mean in a security plan? What is recovery in physical security? How can I assess my property’s physical security? How should I position security cameras for best coverage? What type of security cameras should I use?
How long should I store security footage? How does lighting affect camera performance? How often should I review or update my security plan? What are the most common physical security mistakes?
How do physical and cybersecurity overlap? What’s the easiest way to improve physical security right now?
